Features
Discover the powerful tools that make Keystash the ultimate solution for SSH key and Linux user management
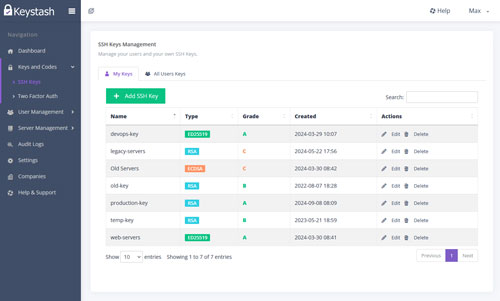
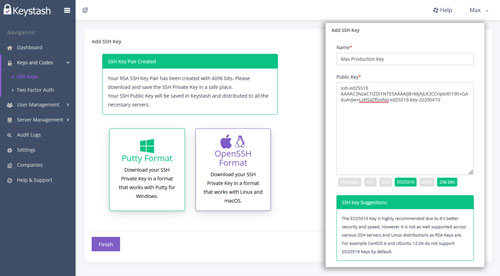
SSH Key Management
Keystash makes SSH key management easy with its intuitive interface. Upload existing keys or generate new ones directly within the platform. Our system guides users in creating strong, secure keys and provides real-time feedback on key strength. Easily distribute and revoke keys across your entire server infrastructure with just a few clicks, ensuring optimal security and access control.
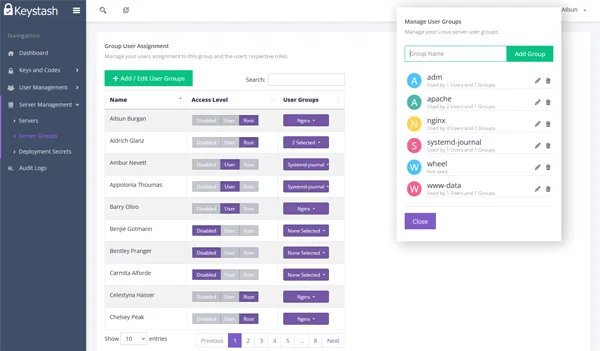
Linux User and Group Management
Take control of your Linux environment with Keystash's comprehensive user and group management. Create, modify, and delete user accounts across multiple servers from our centralized dashboard. Manage group memberships and SUDO privileges effortlessly, ensuring the right access levels for each user. Our intuitive interface makes complex user management tasks simple and efficient.
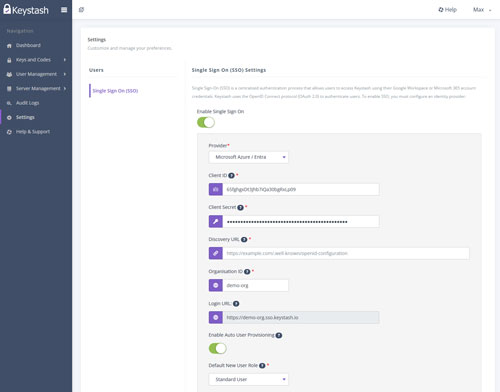
Single Sign-On (SSO)
Streamline authentication and enhance security with Keystash's Single Sign-On feature. Seamlessly integrate with Google Workspace and Microsoft 365, automating the link between your organization's user accounts and Linux user accounts. Reduce administrative overhead and improve user experience while maintaining robust security standards across your infrastructure.
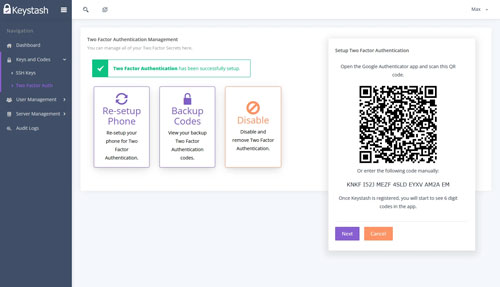
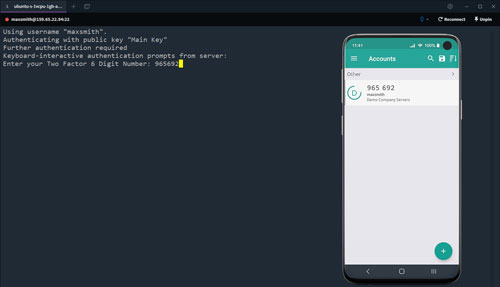
SSH Two-Factor Authentication
Boost your security posture with Keystash's seamless SSH Two-Factor Authentication implementation. Enable 2FA across all your servers with just a few clicks, adding an extra layer of protection to your SSH logins. Our system supports Time-based One-Time Passwords (TOTP), ensuring compatibility with popular authenticator apps.
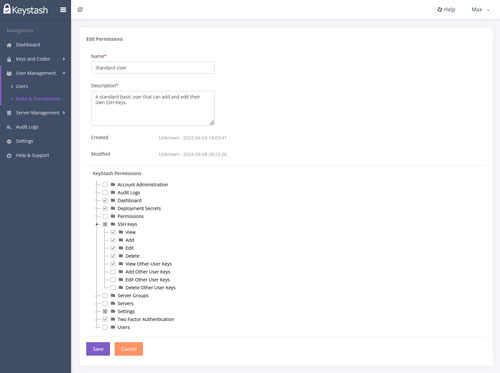
Roles and Permissions
Keystash offers granular control over user access within the platform. Create custom roles with specific permissions, ensuring users only have access to the features they need. From read-only viewers to full administrators, our flexible role-based access control system allows you to tailor permissions to your organization's unique requirements, enhancing security and compliance.
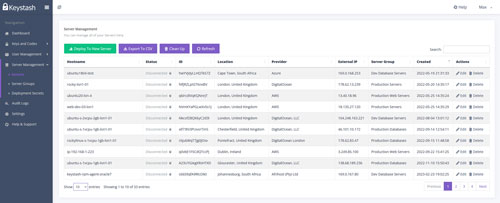
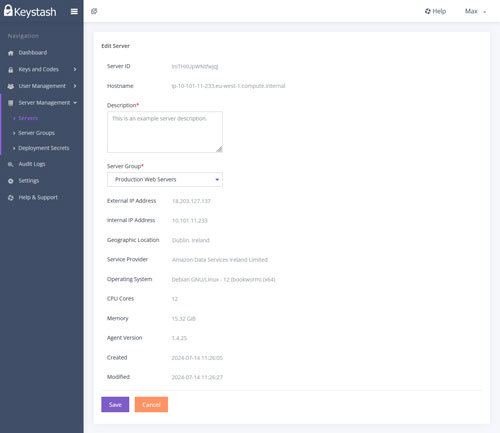
Server Inventory
Gain comprehensive visibility into your server infrastructure with Keystash's Server Inventory feature. Keystash automatically collects and tracks essential details such as hostnames, IP addresses, operating system information, CPU and memory specs, cloud provider data, and geographical locations. Our intuitive dashboard provides a clear overview of your entire server fleet, with easy CSV export capabilities for further analysis and reporting.
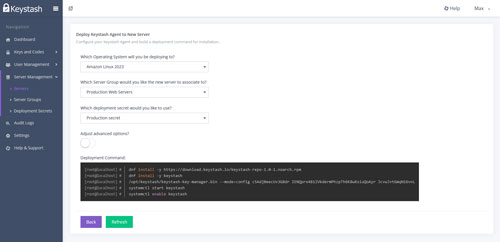
Easy Agent Deployment
Keystash simplifies agent deployment across your Linux infrastructure. Our agent is available through standard APT and YUM repositories, ensuring compatibility with popular distributions like Ubuntu, Debian, CentOS, and Red Hat Enterprise Linux. Monitor agent health status in real-time and deploy updates remotely, all without the need to log into individual servers, saving time and reducing administrative overhead. As the Keystash agent is installed on your servers, SSH logins continue to work even if connectivity to Keystash servers is lost.
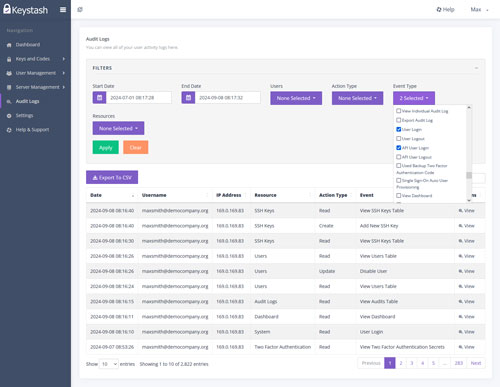
Audit Logs
Maintain complete visibility and accountability with Keystash's comprehensive Audit Logs. Track all user activities within the platform, from login attempts to key management actions and permission changes. Our detailed logs help you meet compliance requirements and provide invaluable insights for security analysis. Easily export logs to CSV format for integration with your existing security information and event management (SIEM) systems.
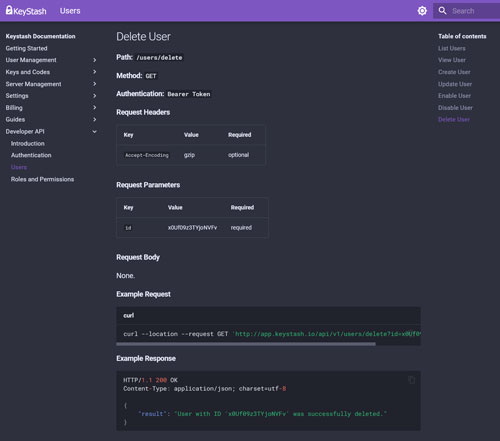
API Access
Unlock the full potential of automation with Keystash's powerful API. Seamlessly integrate Keystash into your existing workflows and tools, enabling automated server deployments, user account management, and SSH server control. Our well-documented API allows you to programmatically manage all aspects of your Keystash environment, from key distribution to user provisioning, making it an ideal solution for DevOps teams and large-scale infrastructure management.
See Keystash in action
Watch a full deployment of the Keystash agent and user onboarding in less than 2min.